Information Security
The processes and methodologies designed and implemented to protect confidential, private and sensitive information from unauthorized access.


IT Infrastructure
It’s a collection of hardware, software, network systems, facilities, and frameworks that enable IT services delivery to different business units and help in maintaining digital presence.


IT Asset Compliance and Certification
IT asset management plays a critical role in helping organizations of to achieve regulatory compliances.


24/7 Support
We are ready to assist you when you need us the most
Free Consultations
We are here to support you with free Consultation
Strategic vision
We'll understand, suggest & shape organization’s technology

We are an IT Consulting & Outsourcing Company
We provide comprehensive consulting solutions to all size of organizations. We offer an array of outsourcing consulting services and delivery engagement models to optimize your spend and staff utilization. Our powerful combination of consulting, technological innovation, and operational know-how yields a comprehensive solutions that will align with your business needs.
Our Services
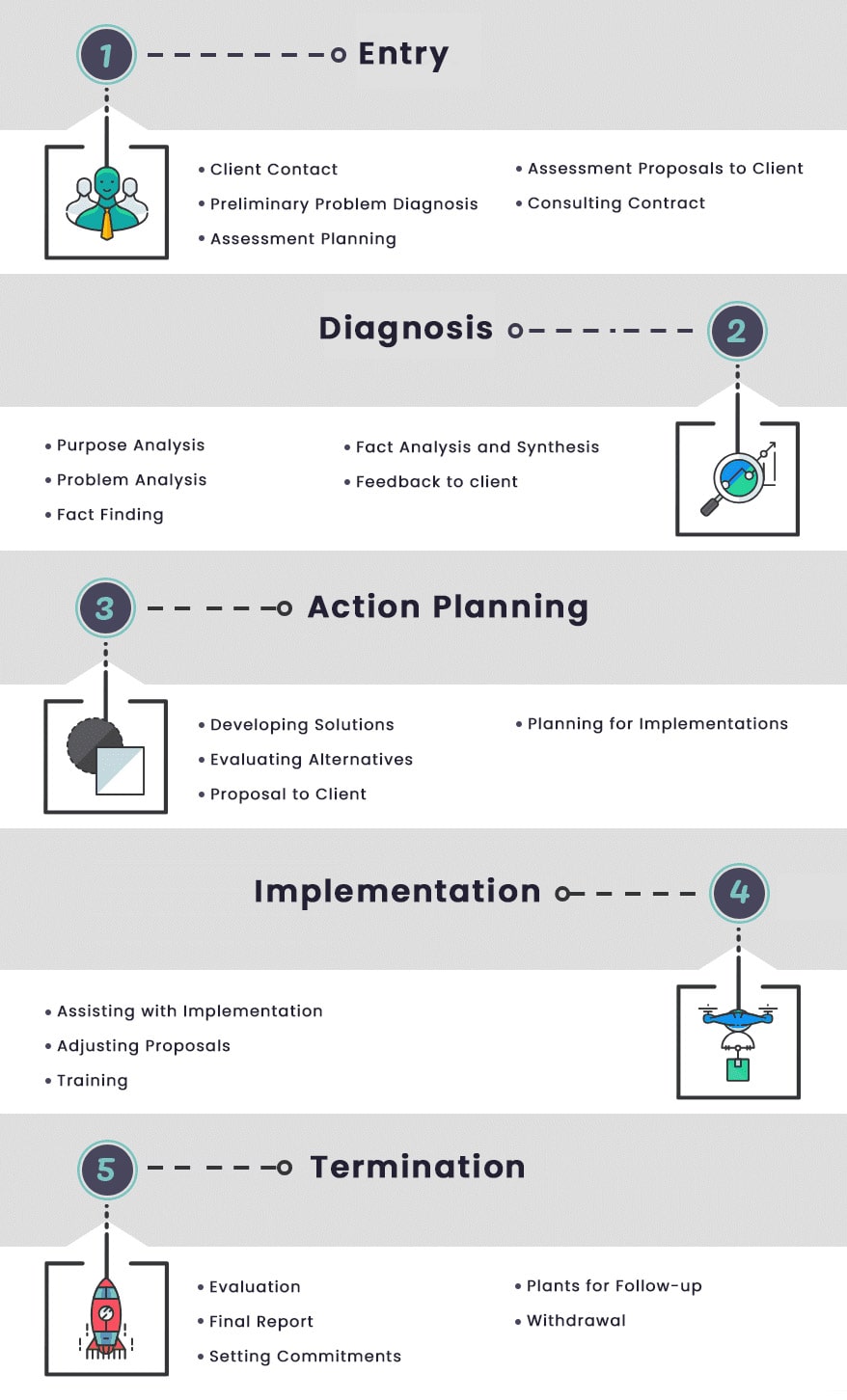
Our Consulting Process
Do you want to grow your business with technology?
Why Us
What We Stand For
We are committed to take you where you want to go and we’ll be with you every step of the way.
What We Value
We believe that success comes from working together, to do good work and serve those around us.
Why We’re Here
We’re deeply committed to everything we do and it shows in the events we host, causes we support and awards we win.

Client Testimonials
Tech Consultant has highly professional and experienced team. They helped us to be ISO & TISAX certified company well on time. I highly recommend all to engage them for any kind of certifications.
Working with Team Tech Consultant has always been a pleasure for us. The guidance and technology insights that they have provided us have been most valuable to allow us to achieve the goals that we have established earlier.
“The vulnerability analysis & Penetration Testing reports, which could only be offered by such a specialist vendor, and the recommendations about how to patch the vulnerabilities are also useful, and Tech Consultant is always helpful when we consult them.”


